VPN (Virtual Private Network) is a well-known acronym amongst regular internet users. Initially, VPN was used in business to connect the network securely. Nowadays, VPN is used by most people for anonymous browsing. VPN can protect user's privacy and stop ISPs and government agencies from tracking their online activities, such as transactions that are looking to capture users performing illegal file sharing of movies, music albums, torrenting, or even trying to access geo-restricted content such as Netflix, Hulu, and other streaming services.
With the exponential rise of internet security threats, it doesn't matter what type of device you are using - whether it's a PC, MAC, tablet, iPhone, Android device, or smartphone - the risk is the same. Every single one of these devices can be tracked and their precise location can be known without any effort.

Below is a diagram showing a typical user accessing the internet without a VPN. The user's IP address is assigned by the ISP and is visible to the internet. Any online resource accessed by the user is completely visible to the ISP and anyone monitoring the user's IP address:
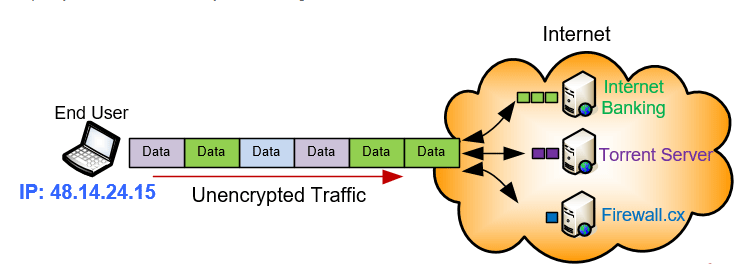
Of course resources such as Internet Banking usually encrypt the data transferred between the client and the server but the traffic source (user IP) and destination (server IP) are still fully visible. Similarly other activities such as Torrent Downloads are fully traceable back to the user.
It should also be noted that ISPs always keep log files of their users'IP addresses. This means that ISPs are fully aware of the IP address assigned to each of their users. By law, these logs are stored for years and can be used as evidence in the event of a law suit or investigation. This applies to home and mobile users.
When connecting to a VPN Service Provider you'll usually be assigned a Shared IP address, that is, an IP address that is used by many users simultaneously. While using a Shared IP address might not sound ideal, it does in fact provide increased anonymity as opposed to using a Dedicated IP address that is solely assigned to your VPN account.
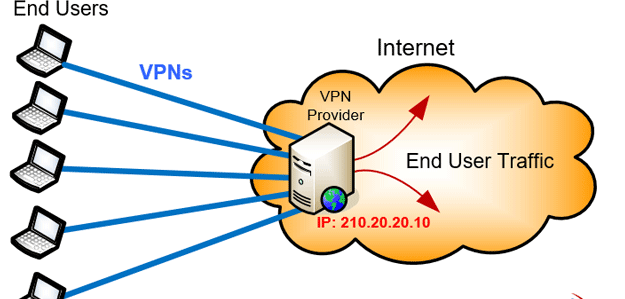
Dedicated IP addresses are usually required when accessing IP restricted servers or websites. Running a website or FTP server off your VPN Service Provider would also be a reason to make use of a Dedicated IP address.
For the majority of VPN users who perform casual web browsing, downloading, file sharing and require anonymous browsing capabilities the Shared IP address is considered a secure option.
IMPACT OF A VPN ON YOUR MOBILE DEVICE'S SPEED, BATTERY OR COMPUTER
Just like any piece of software a well-designed VPN application will function without problems and limit its usage of system resources. There are VPN providers that offer very cheap subscriptions, however, their VPN Client software might be buggy causing either frequent crashes or taking a long time to respond to user actions.
There are quite a few VPN encryption options available through your VPN Client and each one of these will provide you with a different level of security. Stronger encryption, e.g. L2/IPSec, means better security, however, this will have a slightly larger toll on your device's CPU as it will be required to work harder to encrypt and decrypt your traffic due to the high complexity of the strong encryption protocols.
On the other hand, selecting a weaker encryption protocol such as PPTP means that demands on the CPU will be lower but so will the security offered.
Newer protocols, such as OpenVPN, combine the best of both worlds and deliver a fast & secure VPN service at minimal cost to your CPU. OpenVPN is generally the recommended VPN protocol.
As mentioned earlier a VPN makes use of different encryption protocols to secure the connection between the end-user and the VPN server. Selecting the best VPN protocol is important so let's discover the most commonly supported encryption protocols used by VPN providers:
PPTP- Point to Point Tunnel Protocol. Old lightweight VPN protocol which is still very popular but doesn't offer much security. Ideal for streaming and basic VPN needs but not for torrenting.
L2TP/IPSec- Layer 2 Tunnel Protocol & IP Security. The evolution of PPTP offering much better security and encryption at a slight expense of speeds.
SSTP- Secure Socket Tunneling Protocol. A flexible SSL-based encryption by Microsoft. Good alternative to L2TP/IPSec but not as good as OpenVPN.
OpenVPN– a newer open-source VPN protocol that offers great security, flexibility and compatibility. Supported by router firmware such as DD-WRT, Tomato and others.
More servers means better VPN user distribution. This translates to faster servers and fewer users per VPN server.
Higher service availability. If one or many servers go down you'll have plenty of others to connect to therefore limiting the impact on your VPN service.
Ability to access geo-restricted content for every country that has a VPN server available for you to connect to.
Users should be aware that not all encryption protocols offer the same security and performance level. For example, PPTP is an older VPN protocol that doesn't really encrypt the information but simply encapsulates user's data. Think of it as placing a letter (data) inside a standard envelope. The envelope is light so you can carry more of them within a specific period (high performance/throughput). Despite the lower security offered by PPTP, it is still widely used today because not many understand the level of security it provides but also because it's managed to penetrate the market over the past 15 years and is still supported by newer VPN devices and servers.
On the other hand, L2TP/IPSec is the evolution of PPTP and was introduced as an alternative more-secure VPN protocol. It offers significantly higher security but is a slower protocol meaning it has more overhead.
SSTP is a Microsoft proprietary protocol found on all Windows operating systems after Windows Vista Service Pack 1. SSTP is preferred over PPTP and L2TP as it is able to pass through most firewalls without a problem (requires TCP Port 443) whereas PPTP and L2TP/IPSec might not be able to pass through a firewall as they use uncommon TCP/UDP ports which are usually blocked by corporate or guest networks.

Finally, OpenVPN is by far the preferred VPN protocol. It's an open-source (freely distributed) newer technology supported by almost every device and VPN service provider. It's flexible, offers great security, has moderate CPU demands and can run in almost any environment capable of passing through firewalls without a problem.
In addition, the router in our company supports OpenVPN allowing users to connect to their VPN provider at the router level, removing the need for any VPN client software on devices connecting to the home or business network.
Using the right VPN encryption protocol is important as it will significantly affect the security provided as well as your upload/download speeds.
Understanding what a VPN service is and how it can help you protect your online privacy is very important today. Enabling anonymous browsing and protecting your online identity against attack is as equally important as running an antivirus on your computer. VPN Services help provide a significant level of identity protection while at the same time unlocking geo-restricted content with the click of a button. Protect your online transactions and activities with a highly recommended VPN Service today.
USR IOT's cellular routers support secure VPN communications, you can use USR IOT's cellular routers for high-performance connectivity in retail and commercial applications where wired connections aren't possible and industrial applications in energy, transportation, and smart cities that demand rugged reliability. Whether you need a cellular router for your 3G/4G/5G network or looking for a reliable network device for sophisticated computing application, USR IOT's cellular routers are definitely your go! Click here to learn USR IOT's cellular routers: https://www.pusr.com/products/cellular-routers/

